BreachForums - The Return
BreachForums is an English-language cybercrime forum that operates as a black-hat marketplace and community, facilitating the exchange of information about data breaches, the sale of stolen databases, hacking tools, and other illicit services. It was created to replace RaidForums, which was seized and taken offline by law enforcement authorities in 2022.
It was launched in March 2022 by Conor Brian Fitzpatrick, known online as “pompompurin,” shortly after the takedown of RaidForums. On March 21, 2023, the forum was shut down following Fitzpatrick’s arrest. After this takedown, BreachForums re-emerged under new administrators and moderators, including actors associated with ShinyHunters and IntelBroker.
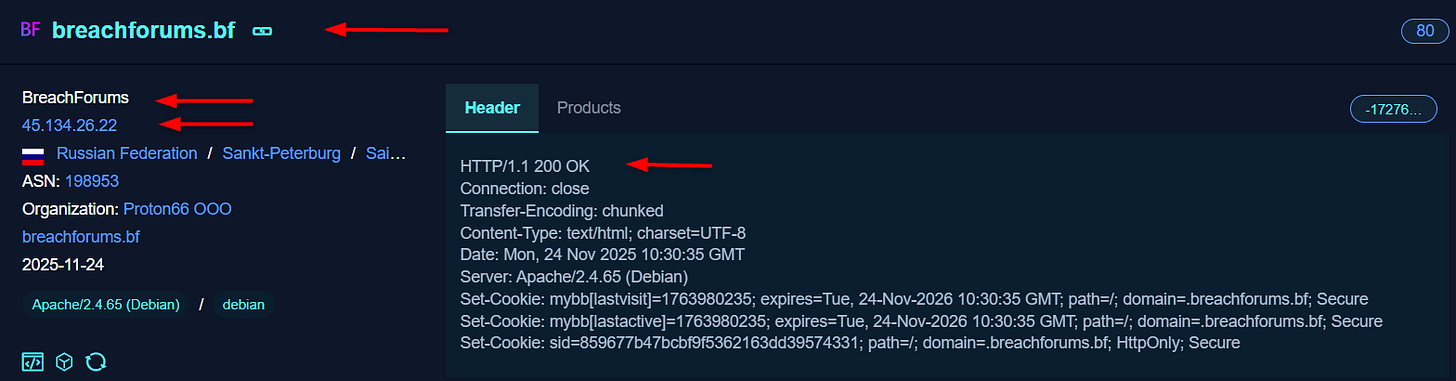
Since then, the forum has repeatedly resurfaced using dozens of domains and mirrors, operating across both the TOR network and various clearnet domains (current is breachforums[.]bf), many of which were later seized or disrupted by law enforcement, which resulted in several cycles of shutdowns and re-launches over time.
ShinyHunters, an established cybercrime group active since around 2020, has been publicly linked to BreachForums as a key actor involved in its revival and partial administration following the arrest of its original founder.
In addition, BreachForums has been repeatedly associated with activity attributed to Lapsus$ and related clusters. In 2024-2025, an overlap between BreachForums infrastructure and actors described as “Scattered Lapsus$ Hunters,” a loose alignment of individuals linked to Lapsus$, Scattered Spider, and ShinyHunters was identified.
This report is an intelligence-driven analysis that correlates technical infrastructure, threat actors, and exposed data to connect disparate indicators and build a coherent intelligence picture. By linking platforms, domains, operational artifacts, and known groups, the report moves beyond isolated findings and contextualizes them within a broader ecosystem, enabling a deeper understanding of how the infrastructure, actors, and activities interrelate and what they reveal about the underlying narrative behind the observed events.
From Dead End to First Exposure
First, I started with the given, the domain name (breachforums[.]bf).
No WHOIS records, it wasn’t part of data leaks or any scraped data, and I couldn’t find any relevant leads based on the official domain name.
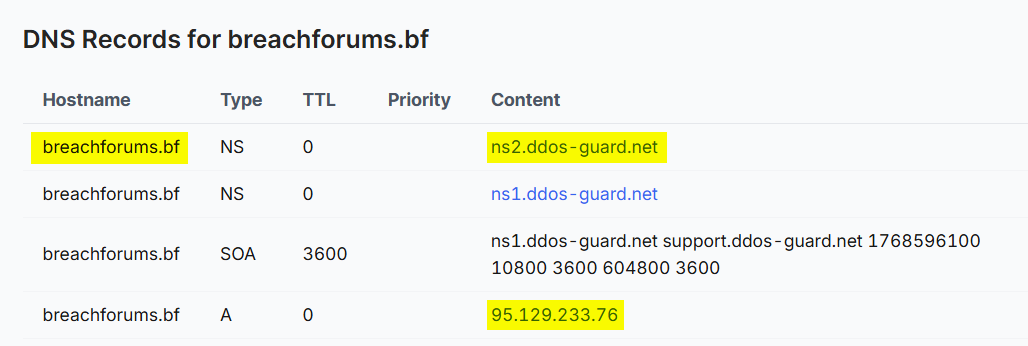
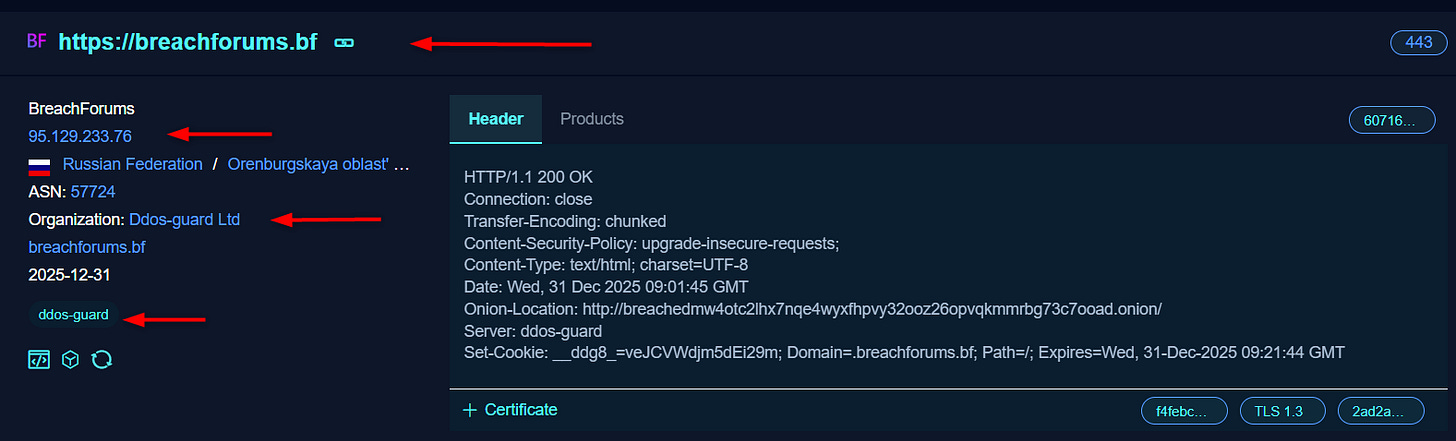
The IP address that was resolved by the domain is 95[.]129[.]233[.]76, and when I searched for it, I saw it’s a DDoS protection service and not the real IP of the domain.
I ran a custom enumeration script (fuzzer) on the domain and found few misconfigurations that led me to status code 200 (HTTP OK), as most of them were unreliable and just refreshed the page to the home page of Breachforums, few led me to see sensitive details that provided me with further understanding about the infrastructure and the assets related to the operation.
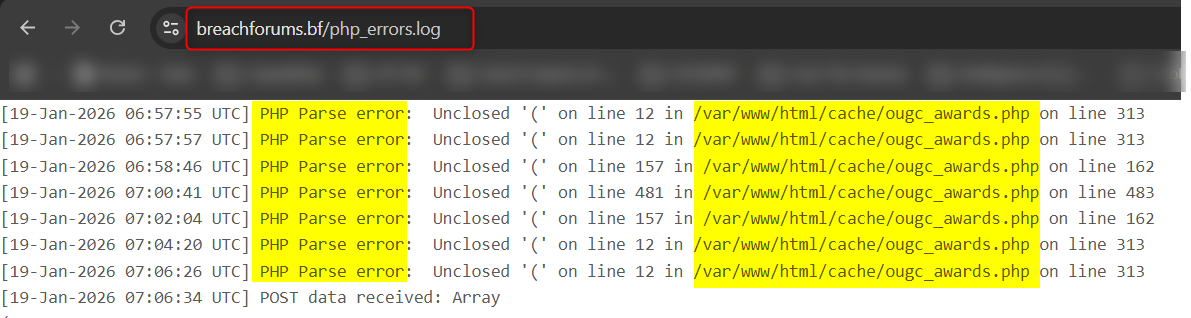
I was able to see the php_errors.log page, publicly disclose the PHP error log containing repeated PHP Parse errors indicating a syntax issue (“Unclosed (”) within a specific file: /var/www/html/cache/ougc_awards.php.
This file appears to be an automatically generated cache file, likely associated with a MyBB plugin such as OUGC Awards. The fact that these errors are logged dozens of times within short time intervals indicates that the server repeatedly attempts to load a corrupted or malformed cache file, pointing to poor maintenance, a failed update, or an improper system configuration.
The log discloses the server’s full filesystem path, precise technology stack (PHP with MyBB), a specific module, directory structure, activity timestamps, and the frequency of recurring errors, all provides the ability to map infrastructure and operational processes, identifying active components and plugins, and collect other crucial intelligence.
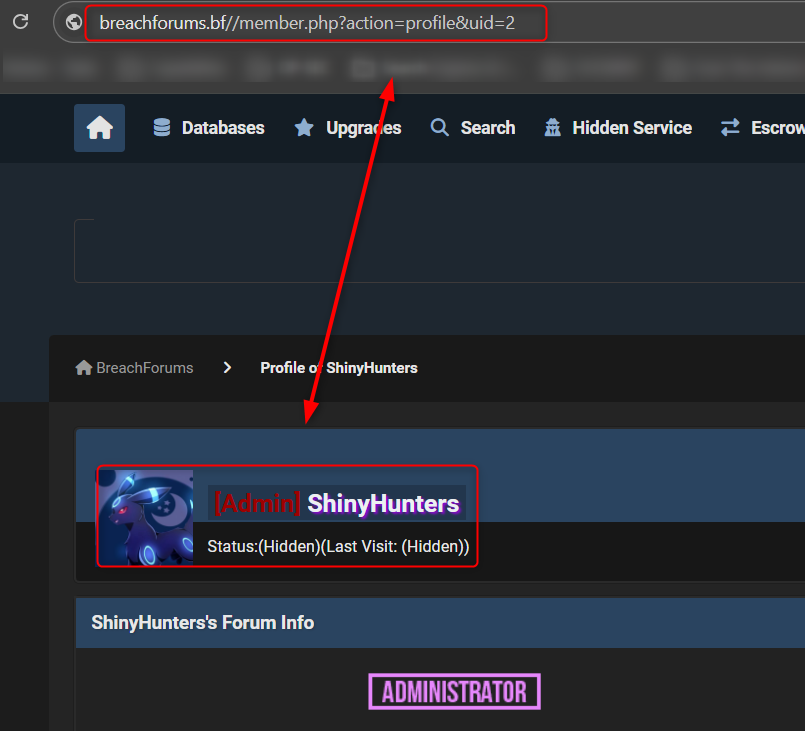
The user enumeration inside the website is not configured correctly and allowed me to view all of the users by their joining date and asses by that who the current admins.
https://www.breachforums[.]bf/ member.php?action=profile&uid=1 provided the admin of the forum, and all I needed is to change the number to 2, 3, and going to check the other users. Number 2, by the way, revealed that ShinyHunters is the admin as well.
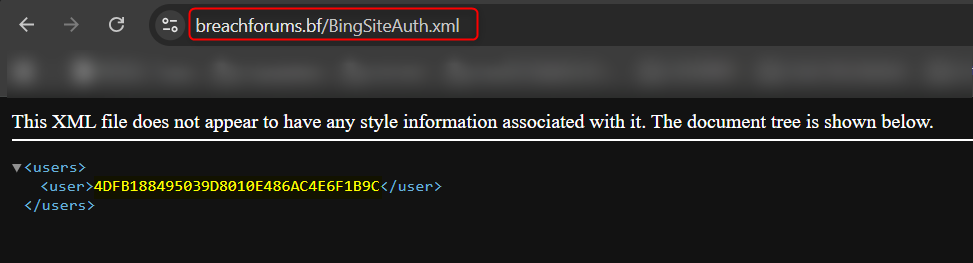
Another misconfiguration that provided me with trustworthy intelligence is the fact that https://breachforums[.]bf/BingSiteAuth[.]xml is widely accessible and provided me with the user's one-time hash for SEO purposes.
The BingSiteAuth.xml file is a standard ownership-verification file used by Microsoft Bing to confirm control over a domain, and its presence indicates that the site operators had (or still have) write access to the web root, reflecting full operational control of the domain at a given point in time.
Beyond simple verification, it confirms the deliberate use of official SEO and webmaster tools, suggesting that the site was intended for indexing, visibility, and sustained presence in search engines rather than being a short-lived or purely temporary deployment.
When correlated with server logs (that already been partly exposed), infrastructure changes, and domain activity, the file can help establish a timeline showing when the site reached an operational stage suitable for public indexing.
Identifying The Operational Core
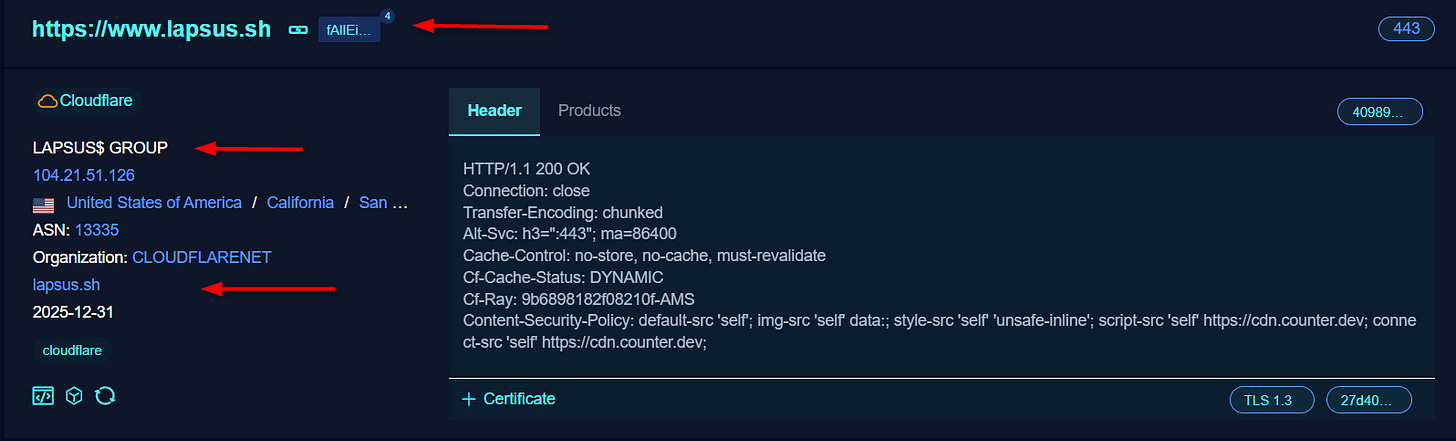
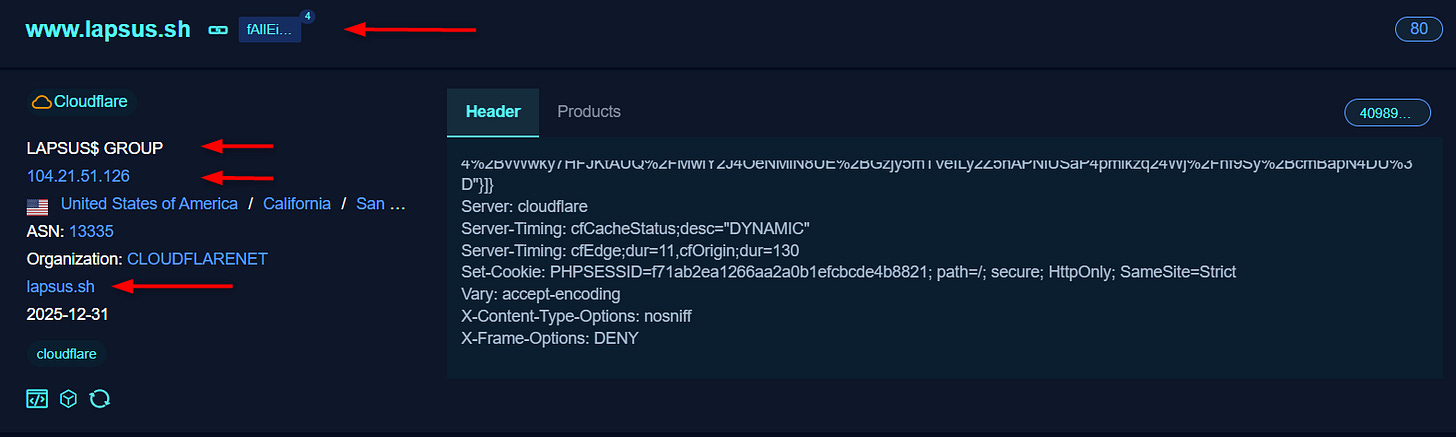
When searching for the domain name using indexing search engines, I noticed the IP repeated IP address 95[.]129[.]233[.]76 (the DDoS guard) and 104[.]21[.]51[.]126, which is directly related to ShinyHunters and Lapsus’ infrastructure, all say it’s not the real IP address I’m searching for.
But one IP address stood out - 45[.]134[.]26[.]22, that leads directly to the domain of breachforums[.]bf.
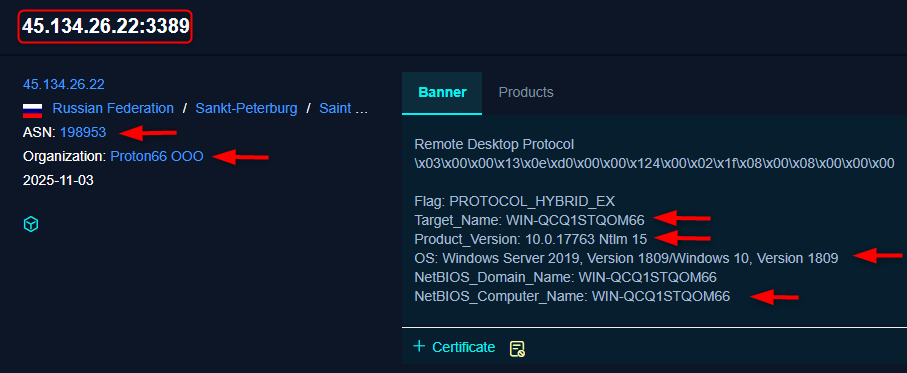
This IP address was exposed in an RDP handshake scan and reveals the remote desktop service (3389), which indicates a Windows server, probably the one that acts as the main station of operation.
The banner reveals detailed infrastructure information, from the IP which belongs to ASN 198953 operated by Proton66 in Russia (Saint Petersburg), the system is running Windows Server 2019 / Windows 10 version 1809 (build 17763), the authentication uses NTLM, and the internal machine identifier (Target Name and NetBIOS name) is WIN-QCQ1STQOM66.
From an intelligence perspective, this constitutes a full infrastructure fingerprint of a management server, exposing OS type and version, internal host name, hosting provider, and geolocation, indicating weak hardening, as we already saw before.
This IP address was shown with port 135 (Endpoint Mapper) and constitutes a strong indicator of a Windows server that is publicly advertising management-related services.
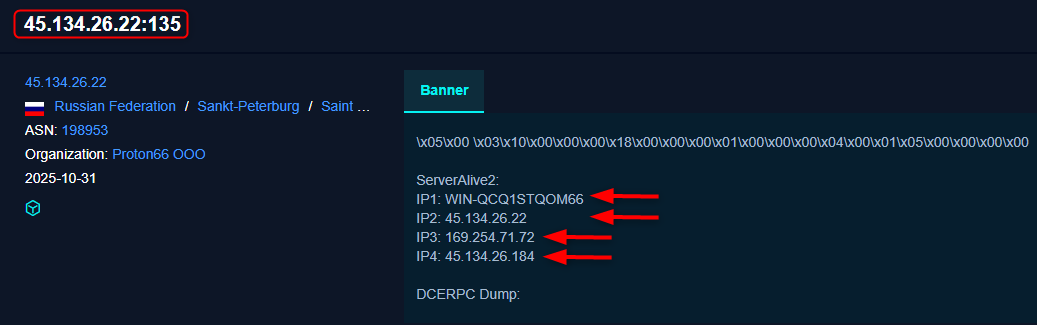
The IP contains data of other addresses shown in the banner, all of which relate to the single Windows host and represent different network identifiers associated with the same system.
45[.]134[.]26[.]22 is the primary public IP address exposed to the internet and the endpoint through which the RPC service on port 135 is reachable. WIN-QCQ1STQOM66 is the internal hostname of the Windows machine, leaked during the RPC/DCERPC handshake, and it serves as the common identifier linking all associated interfaces.
169[.]254[.]71[.]72 is a Windows link-local address, which is not routable on the internet and typically indicates an internal, virtual, or fallback network interface, suggesting the host has additional internal networking configured.
45[.]134[.]26[.]184 is another public IP within the same ASN and address range, representing an additional interface, a closely related node, or an adjacent system associated with the same infrastructure.
All of these are identifiers that show the exposed RPC service reveals a mapped view of the host’s networking, allowing to correlate multiple IP addresses and interfaces back to a single Windows server without any authentication, providing strong infrastructure linkage and insight into the host’s network layout.
These three IP addresses were deeply checked, and I found out that all of them host different domains with (.cyou), all unavailable and registered in 2025 by an unknown entity, probably for malware spreading purposes.
Such domains, for example:
indickensonkas[.]cyou
aesacksis[.]cyou
sashkra[.]cyou
saudkas[.]cyou
indaks[.]cyou
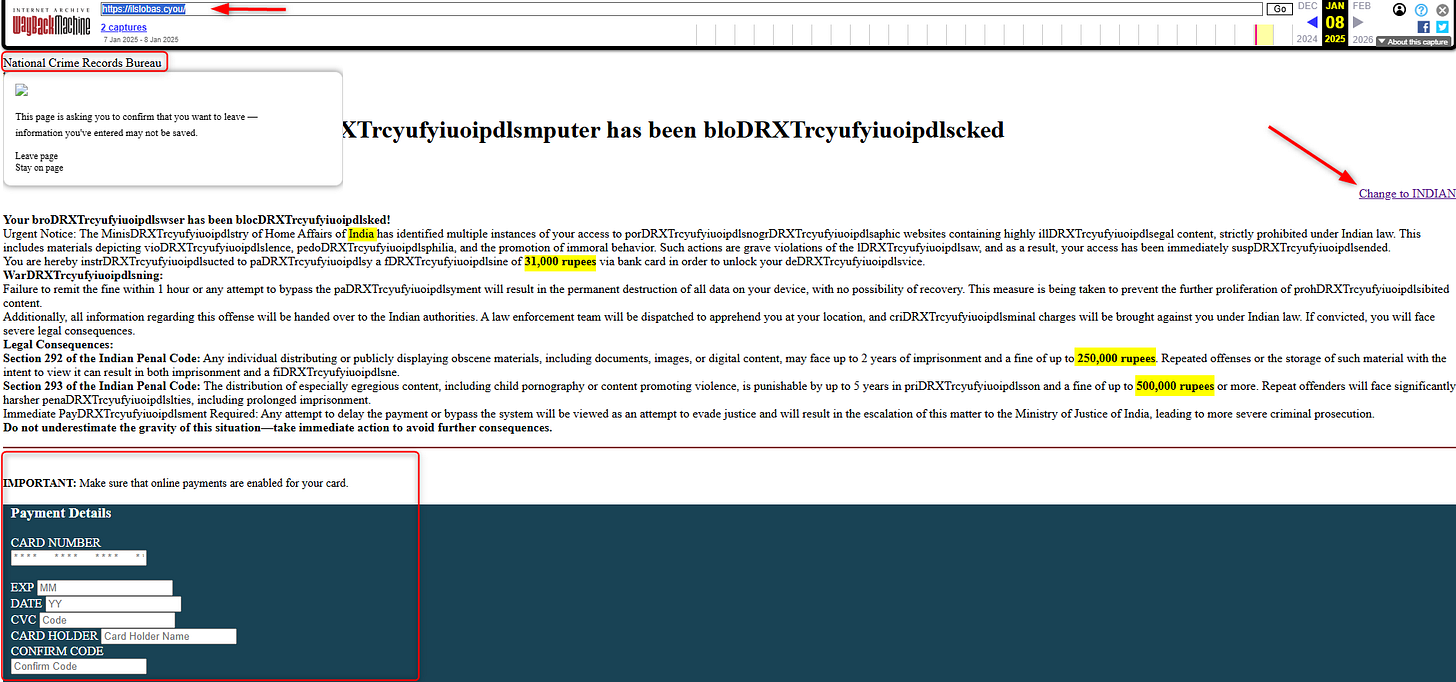
ilslobas[.]cyou
All pages were deleted, but I managed to find an archive for one of them, verifying it is part of Phishing infrastructure, containing payment request informationn and it seems to be dedicated to Indian citizens.
One Hash, Many Faces
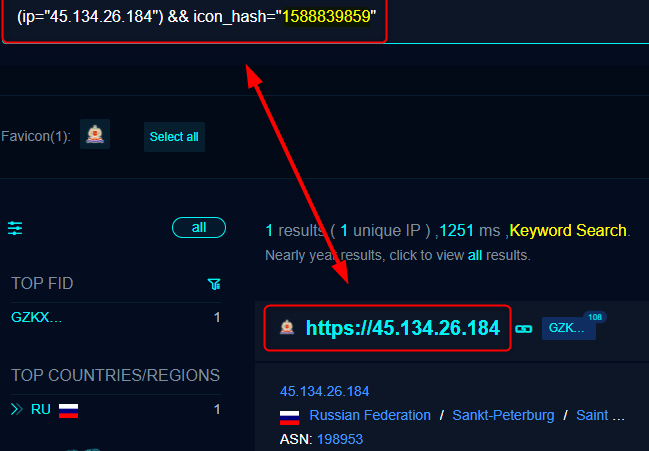
When I deep dived into the address 45[.]134[.]26[.]184, I saw it was directly connected to another website by using the same Favicon hash.
Favicon is an icon a website uses in the browser tab or bookmarks, and the favicon hash is a unique digital fingerprint created from that icon file, meaning that if two sites have the same hash, their favicon files are exactly identical at the file level.
When two websites use the same favicon hash, it means they are using the same default icon, the same website template, the same software or control panel, or were deployed from the same setup or infrastructure.
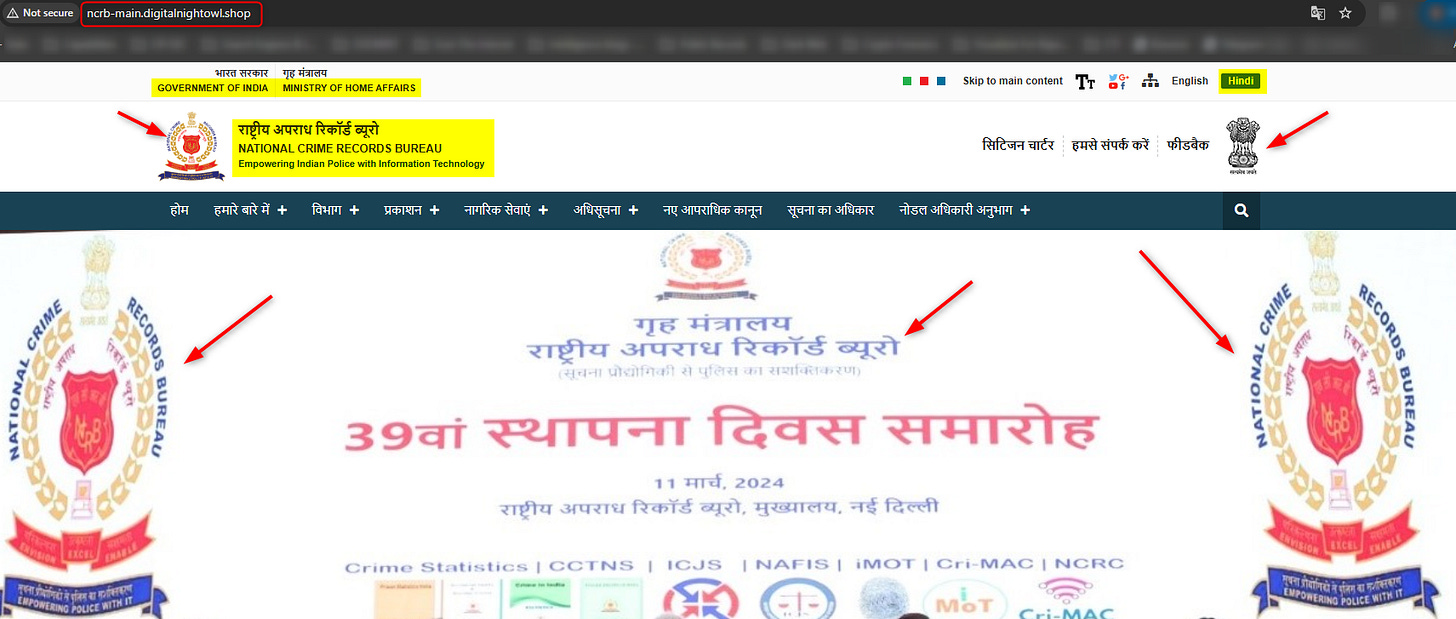
The favicon hash is 1588839859, and when searching who else uses the exact hash, I found out the website ncrb-main[.]digitalnightowl[.]shop, a dedicated phishing infrastructure, impersonating the National Crime Records Bureau of India.
WHOIS records of the domain show the domain was registered in October 2025, using GoDaddy, exactly as the others.
The domain of digitalnightowl[.]shop contains dozens of other subdomains as well, for different purposes, from Banks fake pages, real-estate agencies fake pages, government fake pages, and hotel fake pages, all directed at Indian citizens.
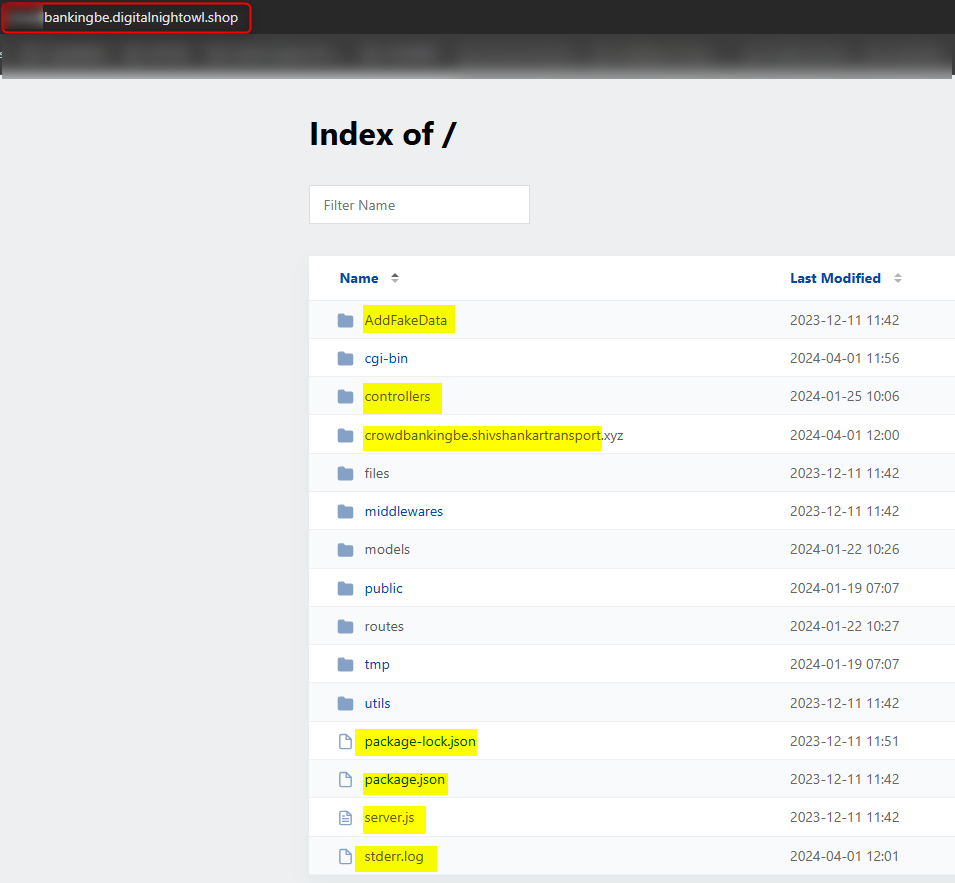
One of the domains had several misconfigurations that led me to see the backend of the website itself, including the JS files, routes, and error logs.
Beyond The Frontend
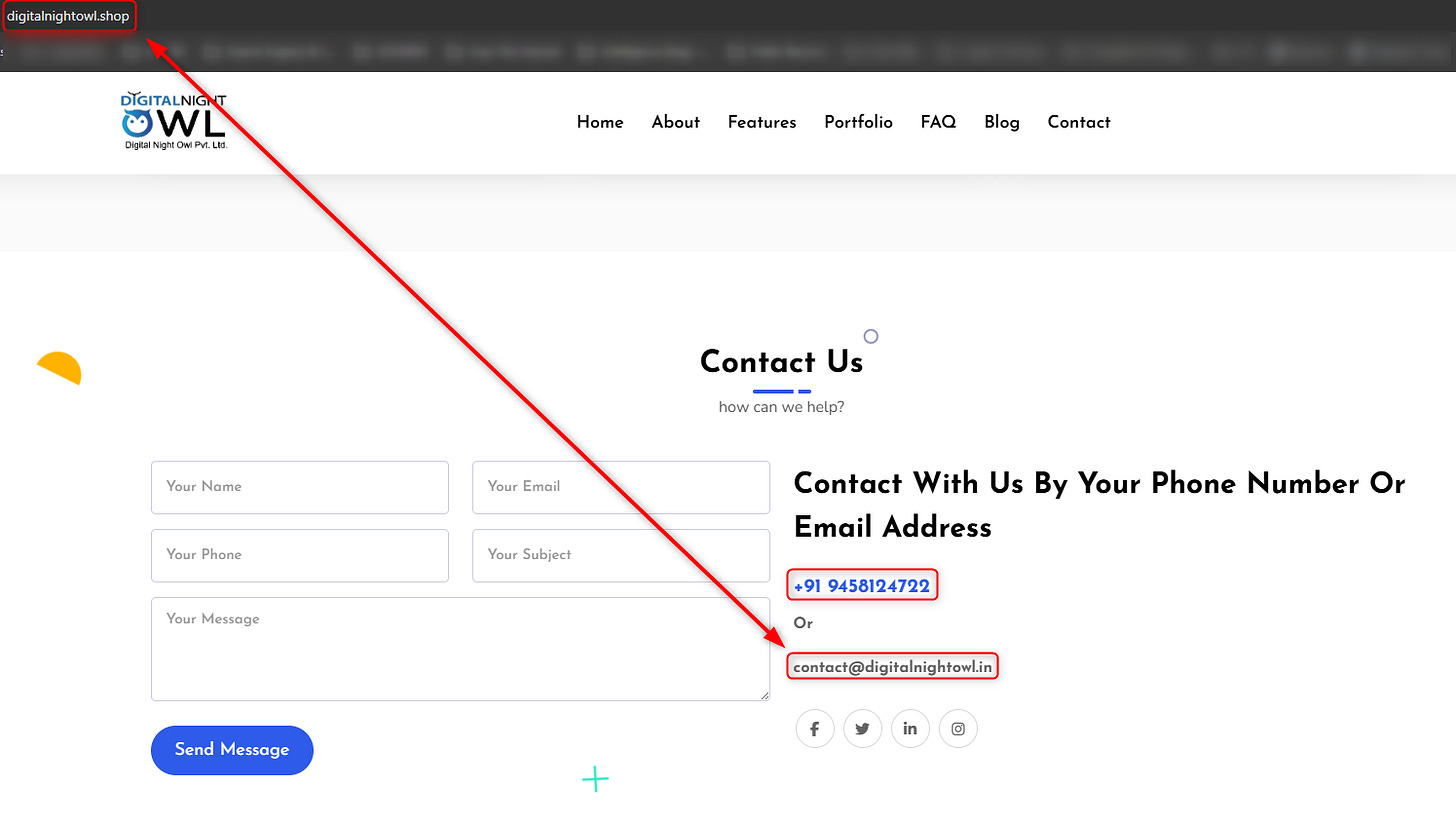
When I started searching about “digitalnightowl[.]shop”, I found references to an Etsy store that wasn’t very useful but when I logged in to the website itself, I noticed the there is a difference between the name of the website itself and the name in the URL, meaning the site is technically served under one domain but displayed or branded as another, usually due to a server-level redirect or domain alias.
This commonly occurs when the same operator controls multiple domains for a single website, for branding, redundancy, SEO, or during a domain migration, or when one domain is used as an entry point while another is defined as the primary logical or canonical domain.
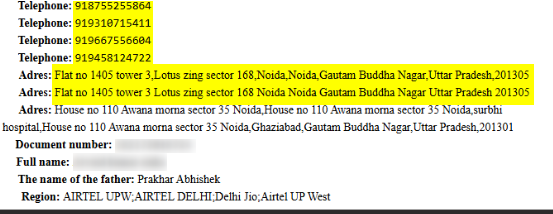
When searching the phone number that appeared on the website, I saw it belongs to an Indian guy named Prakhar Abhishek, probably the owner of Digital Night Owl, a company that seems to be providing service in the areas of IT, Data, and SEO.
The phone number itself was in a data leak from 2025, revealing three other Indian phone numbers and associated addresses under different names, two of the addresses are identical, meaning there is a close relation between these individuals.
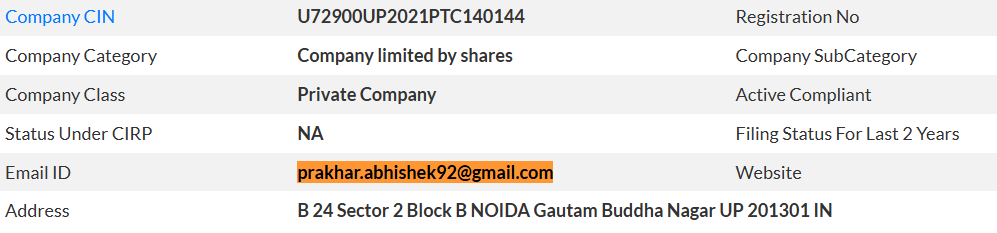
His email address appears in business registrations in India as the owner of the company, which puts him in charge of the operation as well.
The Revival That Wasn’t
What began as an intelligence investigation into the apparent resurgence of BreachForums ultimately led to the exposure of a broad and coordinated infrastructure of impersonation websites designed to defraud citizens in India on a large scale.
Correlation of the findings reveals a consistent pattern in which all indicators converge on a single company based in India, operating in the fields of IT services and digital marketing.
The aggregated evidence suggests that the company’s owners, Indian nationals residing in the country, are likely responsible for managing the entire operation, including attempts to revive the infamous forum, which itself appears to have been repurposed not as a genuine cybercrime community but as part of a deliberate and organized fraud scheme.






hey! this was great. i’ve been loving these. i try to keep my subscriptions super low, but you just added one from me. these deep dives have been fascinating to read.