Who Is Sentap
SENTAP, operating under the alias “sentap.cyber”, is a financially motivated threat actor assessed to have been active since at least 2021. The actor primarily operates as an Initial Access Broker (IAB) and data extortion actor, maintaining a persistent presence across underground forums, encrypted messaging platforms, and email-based communication channels.
His core capability lies in obtaining unauthorized access to organizational environments through compromised credentials, leaked accounts, and abuse of legitimate third-party access. Once access is established, he focuses on identifying centralized file-sharing systems and storage repositories that can be exploited for large-scale data collection.
During 2024 and 2025, SENTAP significantly increased the scale and visibility of its operations, advertising datasets measured in the hundreds of gigabytes. Notable cases attributed to the actor include the sale of large volumes of infrastructure and personally identifiable information linked to NBN Co, as well as a separate dataset attributed to UrbanX.
The data described in these listings reportedly included infrastructure documentation, engineering plans, legal and commercial records, and personal information, highlighting the potential for operational, regulatory, and reputational impact.
Geographically, SENTAP’s activity spans multiple regions, with victims and advertised datasets linked to Australia, Europe, North America, the Middle East, and Asia.
Sector-wise, his operations are cross-industry, reflecting a preference for accessibility and data volume rather than a single vertical focus.
The following research will assess Sentap’s actions, digital footprints, and methodologies to identify who this threat actor is and associate him with a specific country (AKA attribution).
Modus Operandi - Trust Abuse Model
SENTAP’s activity indicates an opportunistic operating model, focusing on organizations with exposed or weakly protected infrastructure rather than highly targeted, bespoke intrusion campaigns.
Following data exfiltration, SENTAP engages in extortion-driven activity, leaving ransom or pressure notes within affected environments and initiating direct communication with victims via encrypted channels.
The actor’s demands centre on financial payment in exchange for withholding public disclosure or resale of the stolen data. When negotiations fail or are ignored, SENTAP has been observed advertising and selling datasets on underground data-leak and marketplace forums.
SENTAP operates as a financially motivated threat actor focused on acquiring initial access to organisational environments and converting that access into profit through large-scale data theft and extortion. His operational model is opportunistic in nature, prioritising exploitable exposure, weak identity and access management practices, and over-trusted third-party relationships rather than sophisticated intrusion tooling or highly targeted campaigns.
Initial access is typically achieved using compromised or leaked credentials, including accounts belonging to internal users and external service providers with legitimate access.
SENTAP also actively identifies and abuses internet-facing assets with weak or misconfigured security controls, such as cloud services, VPNs, and other externally exposed infrastructure, favouring low-friction entry points that do not require advanced exploitation techniques.
Once a foothold is established, SENTAP focuses on abusing trusted relationships to maintain access and expand reach within the environment. By operating through valid accounts, particularly those associated with third parties, he can blend into normal user activity, bypass basic security controls, and access sensitive resources with minimal lateral movement or noisy post-exploitation behaviour.
The core phase of SENTAP’s operations centres on file-sharing and a centralised storage infrastructure. He performs systematic, high-volume data collection and exfiltration, often over extended periods, using legitimate transfer mechanisms such as SFTP or standard download functionality.
The objective is bulk data acquisition rather than selective targeting, enabling the extraction of operational documents, business records, technical material, and personally identifiable information at scale.
Following or during data exfiltration, SENTAP transitions to the pressure and extortion phase. He leaves extortion messages within the affected environment and initiates direct communication with the victim via encrypted and privacy-focused channels. Communications are generally non-aggressive in tone but persistent, emphasising payment to prevent public disclosure or resale of the stolen data.
Signals In Plain Sight
My starting point is the username “sentap”. A lot of details were revealed from different hacking communities under this alias, from BF, to XSS and Leakbase, in all of them he posted dozens of times with different sales offers of stolen data.
I was able to identify two different services he was registered to, Twitter (X) and Matrix (An open network for secure, decentralised communication), that I was able to cross between them due to his usage with the same profile picture as he uses in the different hacking forums he participates in.
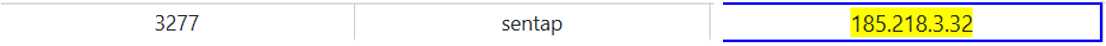
The username led to an IP address, 185[.]218[.]3[.]32, that was directly associated with it, probably as a static IP address.
When searching for this IP address, I was able to find a relevant data breach that contained the IP address, along with the username “sentap” and an email address.
That piece of information revealed another username, a part of the email address, under the alias “hoveylech”, worth checking as well.
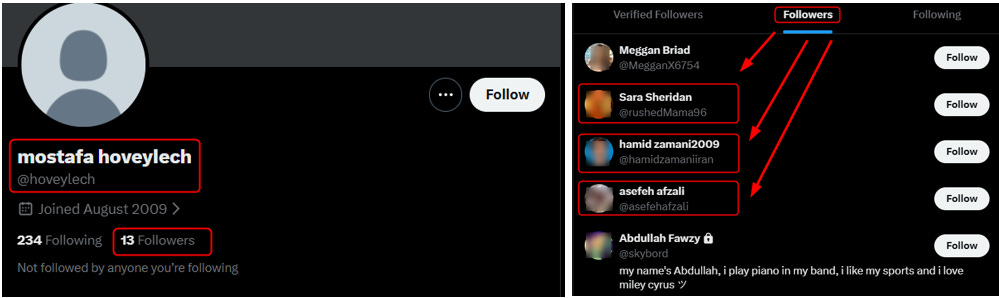
When searching for clues about this username, I was able to find a Twitter account, opened in 2009 under the name “mostafa hoveylech”, an empty account, no posts and no actual activity, but he follows a few individuals that located in Iran.
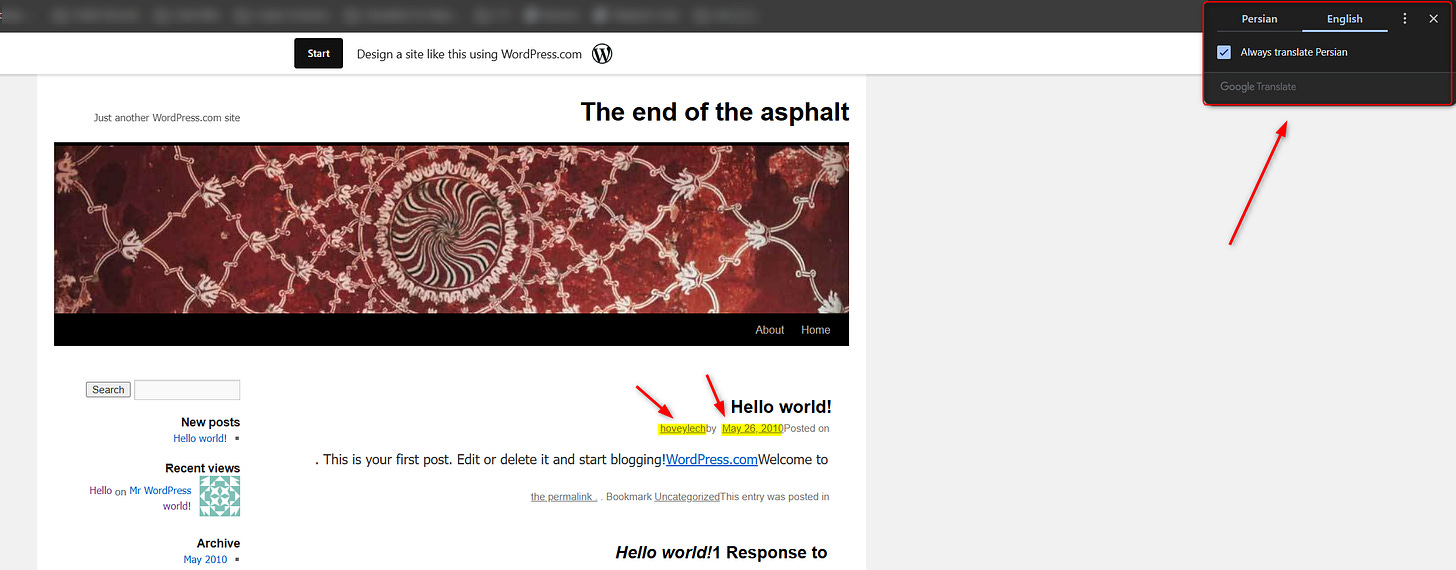
On top of that, I found an old WordPress site created by him, with no data inside. This is a very old creation from 2010, where the threat actor “sentap“ started to operate.
This WordPress website was automatically translated from the Persian language, another huge clue about the possible origin location of the threat actor - Iran.
Names Don’t Lie
Since we have the email address, I started to investigate that lead.
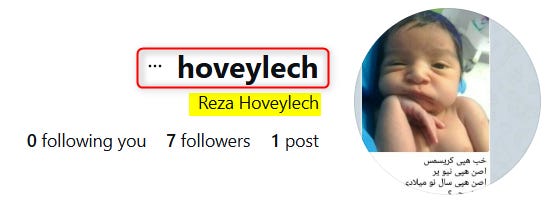
The email address was directly associated with another Instagram account that was opened in 2020 under the name “Reza Hoveylech”.
By the ABOUT data section in this account, the username is “Hoveylech”, and the origin of the owner is Iran, as suspected.
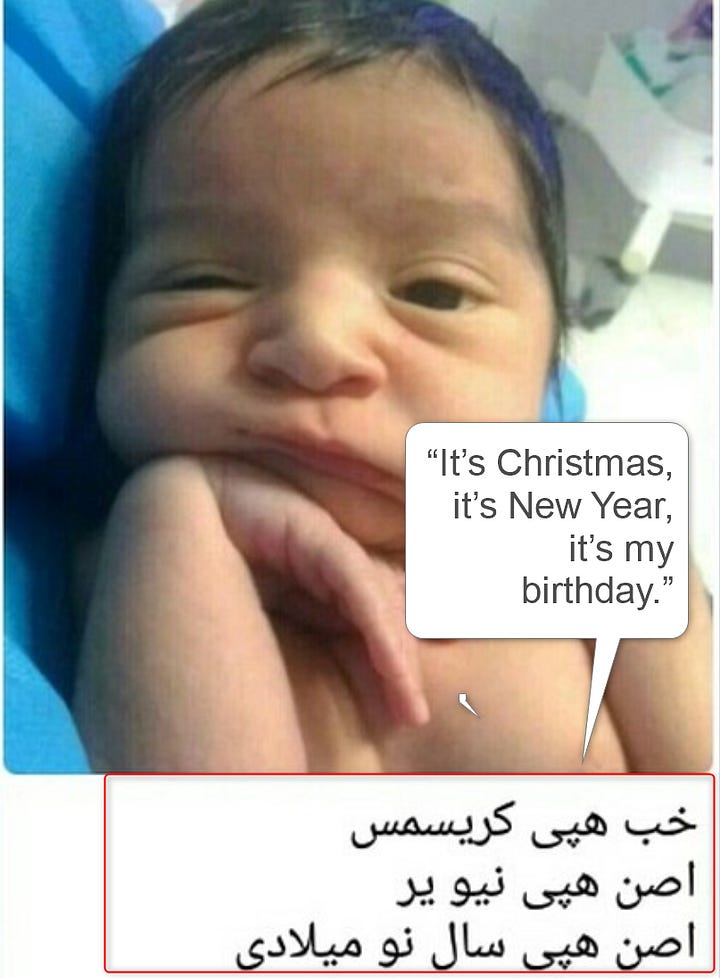
Also, only one photo was published by this account, of a baby with a text in the Farsi language, the official language of Iran.
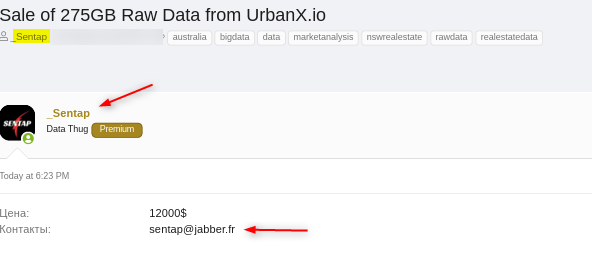
In an archived post of the known hacking forum XSS, I found a post written by him that contains one of his email addresses - sentap@jabber[.]fr, not leads nowhere in terms of data breaches and digital footprint.
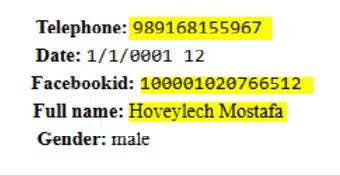
But, the first email address I found is hoveylech@yahoo[.]com, and was part of the major Facebook data breach in 2019, which revealed the Facebook 100001020766512, and revealed two different crucial details – the name “Mostafa Hoveylech”, a name that was already mentioned in the Twitter page that was found, and a new detail -
+989168155967, a phone number with the Iranian country code.
With a deeper dive into the email address, I found a direct association of this data in a database of mcls.gov.ir, the official Iranian government domain belonging to the Ministry of Cooperatives, Labour and Social Welfare, used for public services and administrative systems.
The appearance of the email address in this DB is valid proof that the attribution of this individual is from Iran.
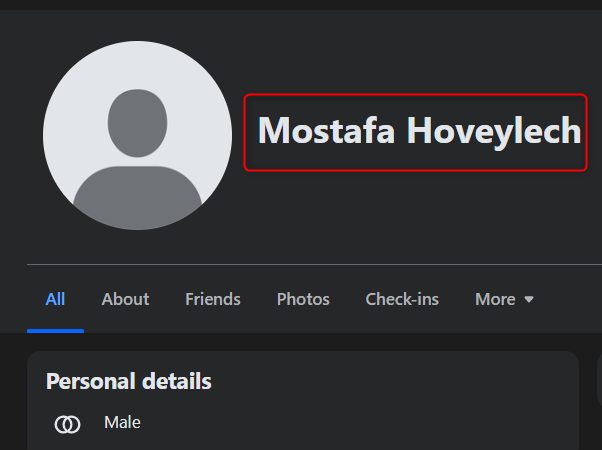
More than that, it reveals his date of birth and validates his full name, as previously mentioned, as Mostafa.
Financial Infrastructure
As the investigation went deeper, by scraping relevant Instagram comments, I found another two profiles of this individual.
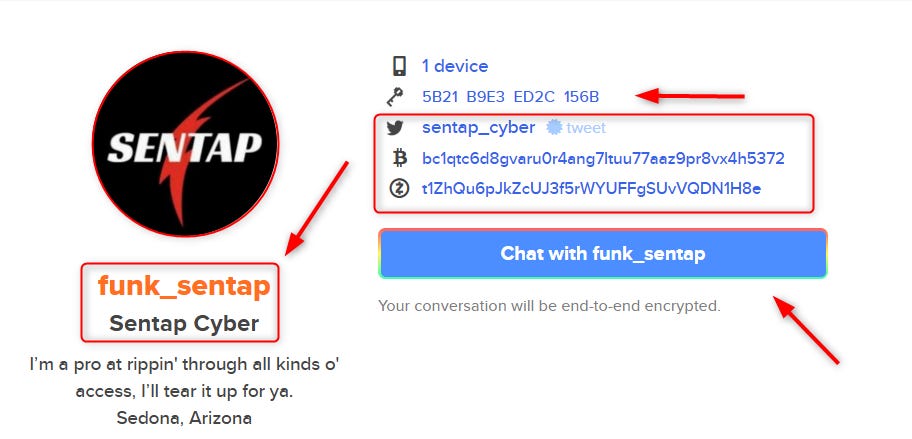
The Instagram page of his persona (“sentap”), followed by the same picture he used in all the other sources, and a reference to his Telegram account.
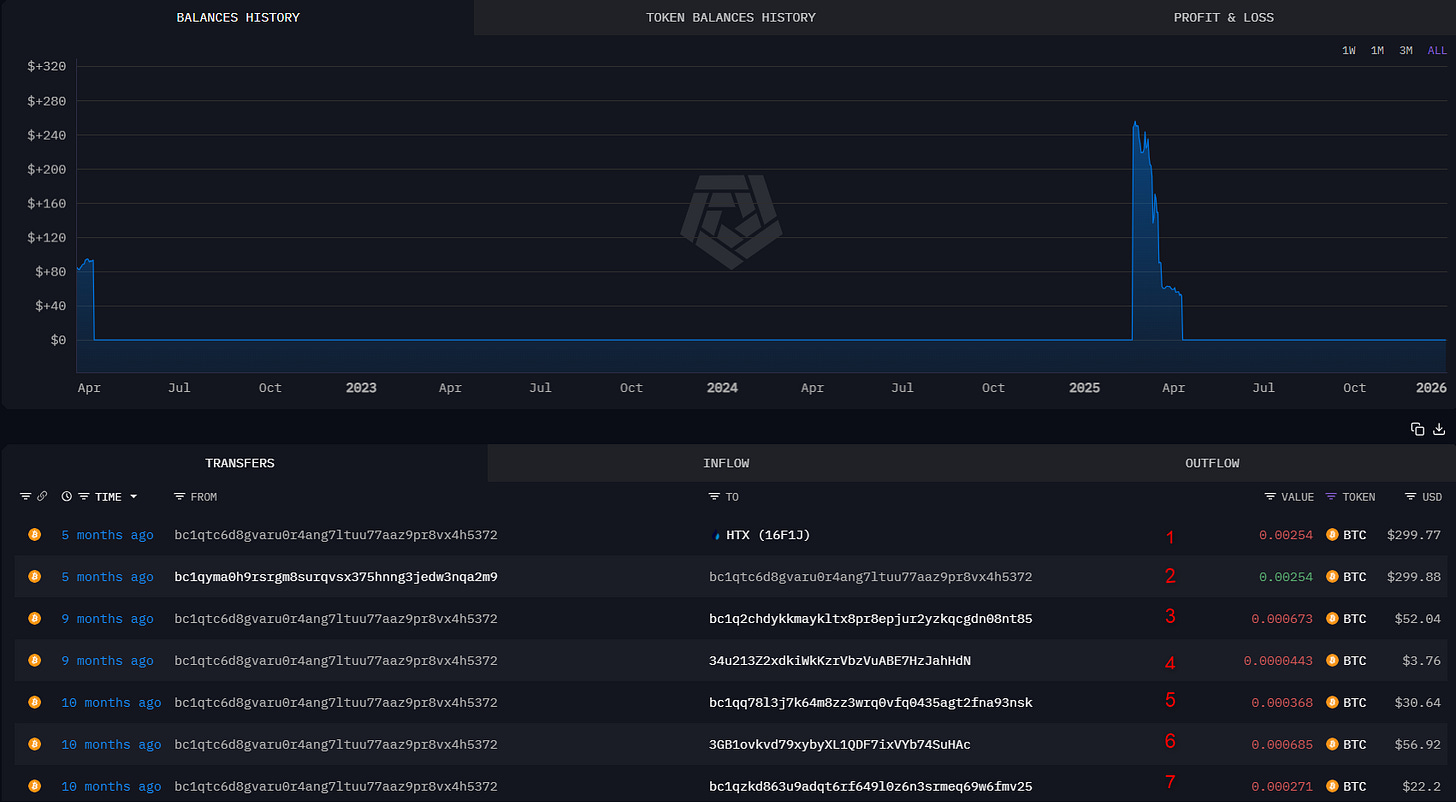
In his old Telegram BIO, he referred to his Keybase profile, where he lists his user, his PGP key, and two crypto addresses.
When analysing the addresses, both showed no more than 300$ in their peak, suggesting no massive illegal activities occurred in association with those.
Relation With Funksec Group
FUNKSEC is a cybercriminal group primarily associated with ransomware operations and digital extortion, which began gaining noticeable visibility mainly during 2024-2025 and operates in a manner resembling the Ransomware-as-a-Service (RaaS) model, combining intrusions into organizational networks with the theft of sensitive data and threats of public disclosure (double extortion).
The group relies on distributed infrastructure, low-cost VPS hosting, compromised cloud accounts, and anonymization services, and typically targets small to medium-sized organizations, educational institutions, service providers, and occasionally government bodies or subcontractors, with an emphasis not necessarily on extracting high ransom payments but rather on conducting a high volume of fast, opportunistic attacks.
FUNKSEC has been observed exploiting known (N-day) vulnerabilities, gaining initial access through leaked credentials or exposed RDP services, using common post-exploitation tools (including Cobalt Strike-like loaders or simpler alternatives), and leaking stolen data via shaming portals or underground forums, positioning the group as opportunistic and not particularly technologically “elite,” yet operationally efficient in scale, automation, and rapid exploitation of opportunities, making it noisy but dangerous, especially for organizations with weak security hygiene.
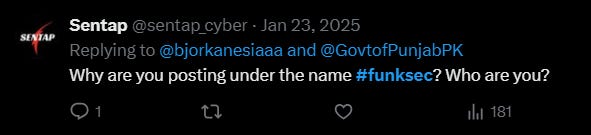
As I managed to find on Sentap’s Twitter page, he commented to a user in January 2025, as he seems as an individual who was part of the group.
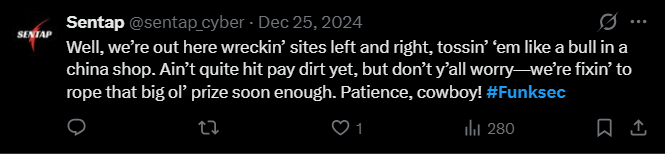
And in December 2024, he officially tags Funksec group in a Twitter post, where he claims to perform hacking activities on their behalf.
Also, when comparing Sentap’s methods and technical abilities with Funksec’s, there is a huge similarity, as they both opportunistically engage with small-sized organizations with the same modus operandi.
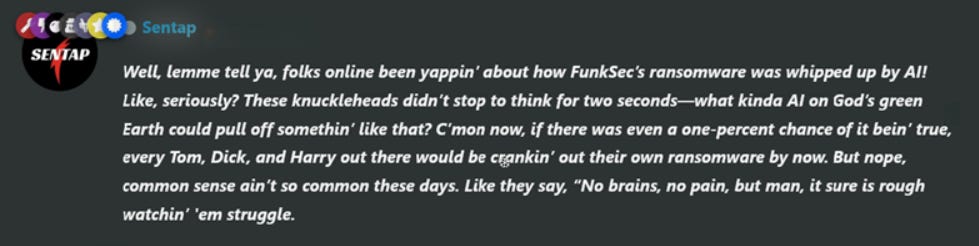
On top of that, in a discussion forum, a comment by Sentap was captured, where he goes against those who claim the hacking software of Fucksec was built by AI agents, dismisses the claim, mocks those spreading it, and emphasizes that, in his view, it is baseless chatter rather than anything grounded in real technology.






really interesting to follow along with this story. great stuff :)
you left me wanting to further investigate this guy haha..