Introducing SPYGAMES, A Web of Digital Exploitation
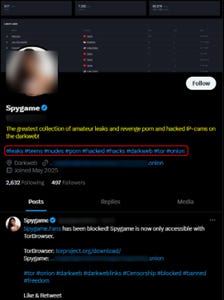
SPYGAME is a transnational cyber-extortion network operating simultaneously on the clear web and the dark web (ONION), known for leaking and monetizing private photos and live camera footage of victims worldwide. The website was first seen in early 2025 under the domain spygame[.]fans, including an ONION mirror.
The platform quickly evolved into a hybrid marketplace for intrusive content and blackmail services.
The SPYGAME ecosystem commodifies the invasion of privacy, offering “Leak & Earn” incentives to contributors, paid “removal” options for victims, and even selling its entire backend as the “SPYGAME PROJECT” package, which includes the site’s code, databases, and hacking scripts for IP cameras.
This report presents a structured OSINT investigation to identify the individuals behind SPYGAME, track its evolution, and document the operational, financial, and technical ecosystem that sustains this cross-platform network.
By combining domain intelligence, blockchain tracing, infrastructure mapping, and digital-persona correlation, the research seeks to attribute ownership, expose infrastructure overlaps, and provide actionable intelligence for law-enforcement and counter-abuse initiatives.
Inside The SPYGAME Network
The network has been active since early 2025, maintaining a small but persistent presence across underground forums, a Twitter (X) channel, and a dark-web community dedicated to leaks and voyeuristic content.
The agenda driving SPYGAME is purely financial, fuelled by an underlying appeal to personal vengeance, particularly targeting individuals seeking to retaliate against women with whom they have had negative or exploitative relationships.
The platform monetizes stolen intimate content through subscription access, extortion payments, and affiliate-style “Leak & Earn” schemes.
Promotional traces of the site have surfaced on different adult-content subforums, where the actors advertise live camera feeds, data packages, and “content removal” services to attract both paying clients and new collaborators to spread the content across the web.
Financial Infrastructure
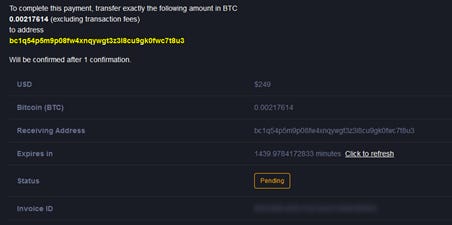
The website offers a “free taste” with blurred content of random girls, but when accessing the actual content itself, including comprehensive guides on “how to hack”, it asks the user to pay for full VIP access.
The requested amount is 249$ for lifetime access, paid via BTC to the following address: bc1q54p5m9p08fw4xnqywgt3z3l8cu9gk0fwc7t8u3
Deep Diving
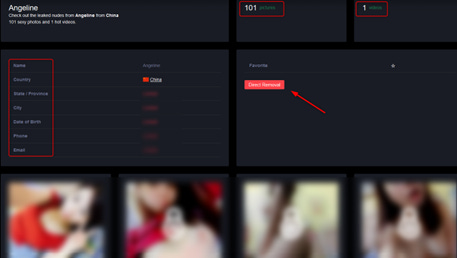
Each content leak of a specific girl contains her personal details as well.
From country to her province, city, date of birth, personal phone number, and email address, all for full disclosure, and obviously, put pressure on her to pay for data removal. In this way, the threat actor always wins, if he is not paid by the content consumers, he gets paid by the victim who is eager to delete his intimate content from the website.
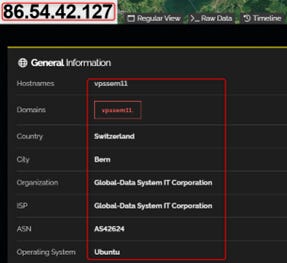
The old IP address of the Clearnet domain (which already got deleted) is 86.54.42.127, leading to a VPS server in Bern, Switzerland. No VPN/Proxy/Cloudflare defenders were identified. The only open ports were 80 & 443 (for web browsing) and 22 (to manage the server itself via SSH).
It’s All About the Domain
When digging in into the old clear web domain of SPYGAMES, 4 different domains were found.
Ø true-leaks[.]com
Ø njalla[.]net
Ø zxc[.]qa
Ø instafansxxx[.]com
Some of them with a clear name indicating the kind of content on those websites, and some seem like random words. Let’s check them deeply.
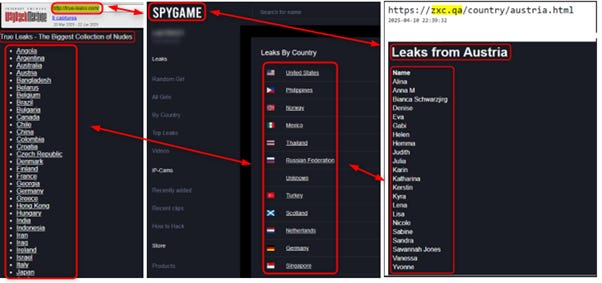
The domain true-leaks[.]com, owns a very suspicious name, almost having direct association to the conspiracy just by the name. Most of them are not available anymore, but older archived versions of them indeed revealed a direct connection to the content on SPYGAME and the same web design and patterns (colour, font, and country list).
In the picture: True-leaks[.]com, SPYGAME and zxc[.]qa websites
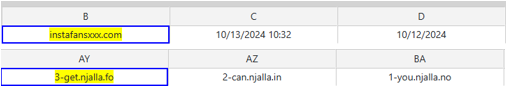
When checking the domain njalla[.]net, it revealed an anonymous domain name registrar, hosting provider and VPN provider, established by The Pirate Bay co-founder and allows an encrypted tunnel from the original computer to the Internet.
Also, it’s the exact registrar that instafansxxx[.com] used to register the domain.
Revealing the Master of Puppets
When understanding that all the domains are associated to another, and of course to SPYGAME, I have dived deeply into them to reveal the individuals associated with to them.
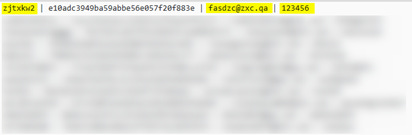
The domain zxc[.]qa was found in association to a few data leaks and revealed the password “zjtxkw2” and “123456”, at least on of them is kind of unique and may be used to reverse search by leaked passwords to find more details. So that is exactly what I did.
The password “zjtxkw2” was found numerous times in direct association with an email address: fasdzc@zxc.qa
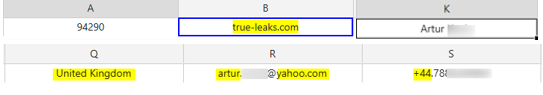
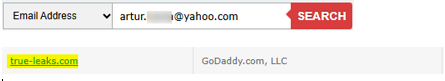
The domain true-leaks[.]com was deeply investigated, and appears to be registered by a male, originally from the UK, under the name “Artur”.
And as shown in the Domain search engine:
Eventually, Anonymity Always Fails
What this investigation really shows is simple and chilling.
Massive criminal schemes don’t fail because their code is bad or their planning was amateur. They fail because people slip.
A reused email at sign-up, an overlooked EXIF tag in a hurried upload, or a careless “like” on a social post, each is a tiny, human mistake that leaves a trail.
When you stitch enough of those crumbs together, domain histories, leaked passwords, blockchain trails and offhand social signals, the mask comes off.
The takeaway for investigators is hopeful and urgent.
Persistent, patient OSINT turns small errors into big breakthroughs, and for those who think anonymity is guaranteed, sloppy OPSEC is not protection, but an open door.