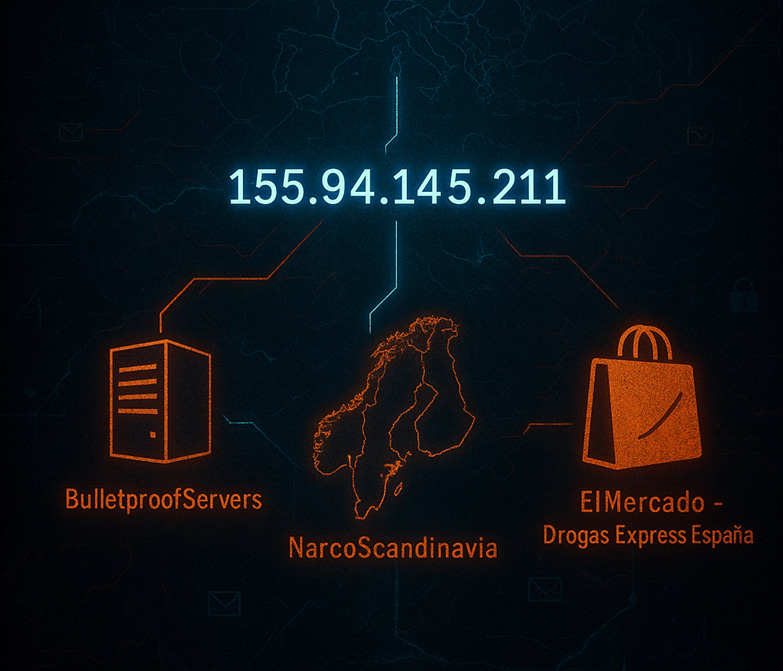
One IP, Three Faces
Behind an ordinary-looking IP address lies a machinery of logistics, distribution, and anonymity, intertwined with surgical precision. Each service masks itself behind a different facade, yet their trails converge unmistakably at the same destination. What emerges is not coincidence, but the blueprint of a coordinated criminal-grade infrastructure.
Three so-called different services, one illicit and the others controversial, act as one part of a faulty and criminal network.
The following report examines a tightly connected cluster of services that operate across the same infrastructure layer and share a common operational footprint. Although each brand presents itself as a separate entity with a distinct purpose, all of them resolve to the same IP address, indicating a unified backend, shared operators, or a consolidated management structure.
By analysing the hosting patterns, network behaviour, and thematic consistencies, the research demonstrates how these services function as interdependent components within the same criminal-grade digital ecosystem, possibly operated by the same owner (s).
The IP Address and Its Services
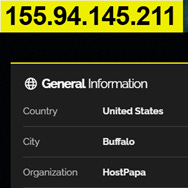
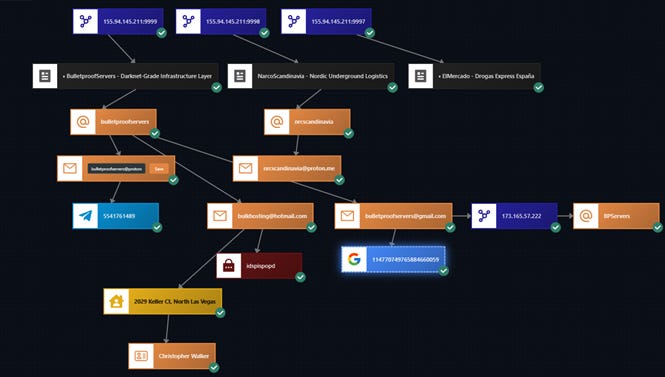
Starting with the IP address 155[.]94[.]145[.]211, I found the three different services hosted at the same address.
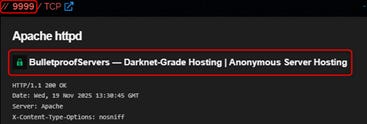
BulletproofServers - Darknet-Grade Infrastructure Layer
BulletproofServers is the foundational layer of this ecosystem. It’s a hosting environment designed for resilience, anonymity, and persistence. This type of hosting prioritizes customer privacy over compliance and offers infrastructure that remains online even under governmental pressure, legal complaints, or even takedown attempts.
The service promotes “darknet-grade” capabilities, including anonymous setup, no identity verification, permissive content policies, full port availability, and flexible server locations.
In practice, it operates as an infrastructure-as-a-service model for actors requiring stable but anonymous digital real estate.
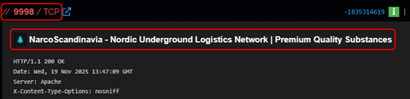
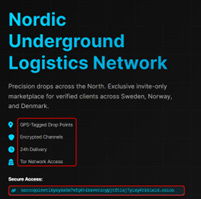
NarcoScandinavia - Nordic Underground Logistics Network
NarcoScandinavia functions as the mid-stream logistical node within this shared infrastructure. It frames itself as a coordinated logistical network operating across the Nordic region, connecting inbound supply routes with last-mile distribution mechanisms. The brand emphasizes structure, reliability, and systematic distribution, qualities associated with organized logistics cells rather than ad-hoc operations.
This part of the ecosystem bridges international supply flows with domestic demand points, using both physical and digital mechanisms: communication channels, shipment coordination, encrypted operational management, and networked courier elements. Its presence on the same digital infrastructure suggests that logistics management, customer coordination, and backend administration are handled through a centralized system.
ElMercado - Drogas Express España
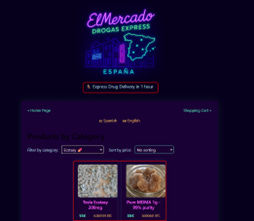
ElMercado represents the frontend, the actual service. It’s a consumer-facing layer of the system. An express-delivery model designed for the rapid fulfillment of different illicit drugs across major Spanish cities. The branding aligns with contemporary “quick-commerce” aesthetics - fast delivery, urban coverage, and on-demand availability, but applied to illicit products.
Operating on the same backend IP, ElMercado appears as the retail endpoint of the ecosystem. While BulletproofServers provides the infrastructure and NarcoScandinavia supports regional logistics, ElMercado translates these capabilities into a commercialized street-level distribution model aimed at end users.
While BulletproofServers offers the durable, anonymous backbone, NarcoScandinavia manages movement, routing, and distribution across northern Europe, and ElMercado provides fast, city-level delivery and customer-facing access for illicit drugs.
Financial Infrastructure
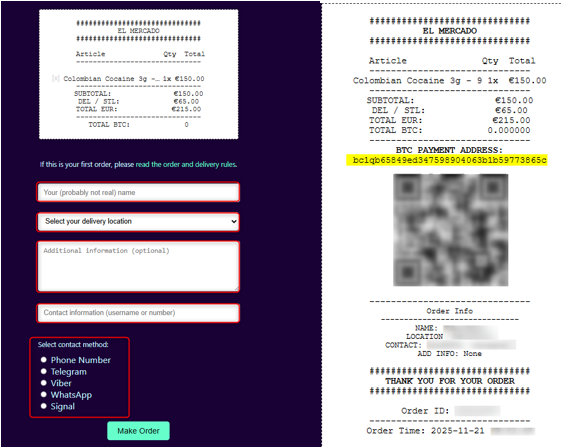
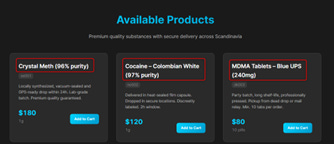
Once the customer chooses the product he desires, he adds it to his cart and proceeds to the payment.
A new tab opens, asking for the contact method the user prefers, for them to contact first via WhatsApp, Signal, Telegram, Viber or a simple phone call.
Such a method indicates a good OPSEC behaviour, eliminating the chance of investigators obtaining their main usernames and contact methods until they will decide to do that (probably after they perform a background check to ensure their safety).
Once the user has completed his contact details, a new BTC address appears in the payment request to deny the possibility of tracing previous transactions associated with the address.
And Way Down We Go
With the known fact that claims the IP address as the backbone of these three services, I started the investigation with the first one, called “NarcoScandinavia”.
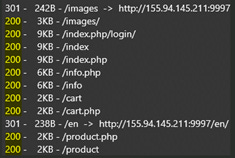
I tried to get as many details about the interface of the website, so I gave a try do web directory search enumeration, to check the different optional pages that answer with a positive response (200), just to find out there aren’t so many of them, and those that do, lead to the same pages I already visited.
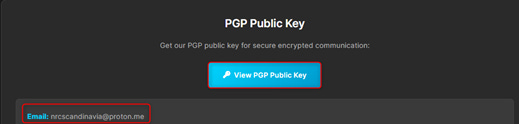
In the “contact-us” page, there is a proton email account nrcscandinavia@proton[.]me, which yielded no results. It wasn’t in any data leaks, any registration, no web mentions of any kind and zero results at all.
I gave an honest try to the username itself “nrcscandinavia”, which also led to no where. This is not the right approach.
When trying the second service, called “bulletproofservers”, I started with the name itself and combined various user search manipulations and different dorks to find leads, since there is no actual domain name but only an IP address with a specific port.
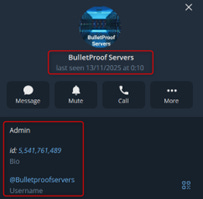
The username itself led to an email address (bulletproofservers@protonmail[.]com), and the Telegram user (bulletproofservers), claiming he is the ADMIN in his BIO.
Not So Bulletproof After All
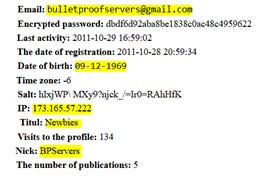
The username was part of a known data leak from a famous hacking group in 2014, revealing a GMAIL address with other details such as DOB, IP address and a user handler in this specific forum.
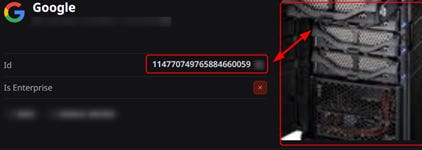
The email address, associated with a Google ID (114770749765884660059), appears with the photo of the service’s logo.
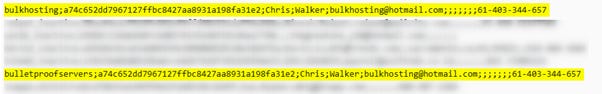
The username appeared in a data leak from 2019 as well, directly connected to another email: bulkhosting@hotmail[.]com, shown with details such as password, address, zip code, city and name of brand called “GameTsunami”.
When checking the brand “GameTsunami”, it appeared as a kind of hub for video gaming, nothing related to bulletproofservers.
The email address was the main thing, and the idea was to find other associations with it, from data leaks to registrations, web mentions and social media activity.
In a leaked database from 2020, I was able to find the above username and the email, in direct association with a name and what seems to be a phone number.
Finding The Owner
Once we got the name of the person associated with the email address, we already have one more crucial detail: a full address.
When using web search manipulations, I was able to get a deleted page (not archived unfortunately), that was still partly available due to cache memory.
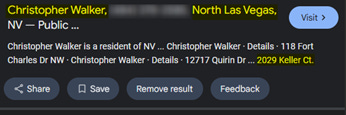
In this search, I was able to find the full name of the individual (Christopher Walker, or as he appeared in the data leak by Chris Walker), and to prove he was a resident of this exact address and sold earlier in 2025.
And the home itself:
Infrastructure Convergence Map
This section visualizes the underlying relationship structure connecting all identified entities across the network. By mapping IP addresses, domains, email accounts, social handles, and operational identifiers, the diagram demonstrates that services which appear unrelated on the surface, BulletproofServers, NarcoScandinavia, and ElMercado, are in fact interlinked through shared infrastructure, overlapping contact points, and recurring digital identifiers.
The graph reveals a consolidated backend ecosystem tied to the same operators, highlighting how infrastructure, logistics, and retail-facing services converge into a single coordinated operation.