Zagros Platform
The “Zagros” service, operated by the Amn Pardaz Nasr Zagros Company, is an officially declared Iranian product designed to provide a domestically controlled solution for accessing the global internet. Its primary purpose is to enable users within the Islamic Republic of Iran to bypass international sanctions and government filtering/blocking of online systems and websites.
The service is explicitly described as an Iranian product offering “unrestricted access to sites and systems that are sanctioned or sensitive to the IP address of our country (Islamic Republic of Iran)”. Technically, it is presented as an alternative to often insecure external tools, aiming to “eliminate the need for... any filter breakers and insecure VPN services” and prevent data leakage in sanctioned or sensitive services.
This strongly suggests its operation as a sophisticated DNS resolver or a similar centralized proxy infrastructure that offers a regulated and monitored channel for external access while being marketed to key demographic sectors such as programmers, graphic designers, gamers, students, and digital currency activists.
Despite marketing itself with features like “Sustainable security” and “Global END to END encryption”, Zagros’s privacy policy contains a critical provision that indicates potential state surveillance and control. While the service claims to protect user privacy, its terms confirm that the service provider has access to users’ personal details, including full name, phone number, and password. Crucially, this sensitive data “will be provided upon official request from competent authorities”. This policy guarantees that Iranian security or intelligence agencies have a clear, documented path to obtain the identity and activity data of any user, effectively centralizing control over the circumvention process and raising serious concerns about surveillance for political activists or others deemed a risk to the regime.

Infrastructure Doesn’t Lie
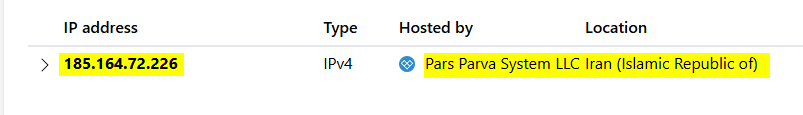
The IP address of the website is 185[.]164[.]72[.]226, hosted by Pars Parva System LLC, Iran, a data provided by NSlookup search.
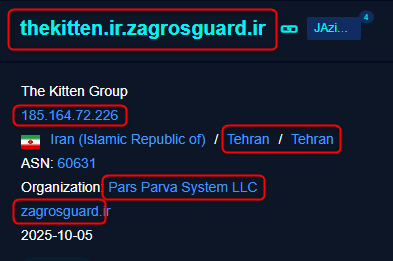
While searching other entities using the IP address, I found a domain named “thekitten.ir.zagrosguard.ir” with the same IP address, the same ASN.
The obvious mention to thekitten[.]ir is a direct link to thekitten[.]group, a covert pro-Iranian infrastructure designed to support cyber warfare and espionage against Israeli and other targets. This platform functions as a sophisticated communication hub aimed at coordinating hostile cyber activities by different pro-Iranian groups.
Hi Kitty Kitty
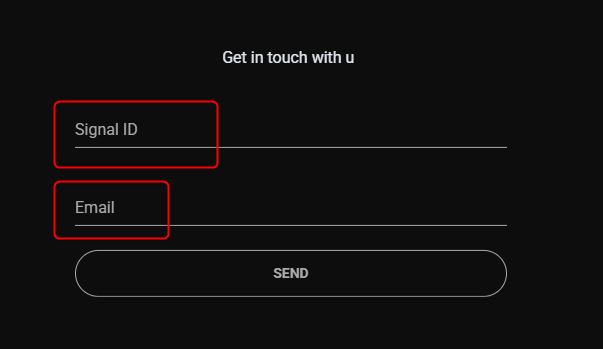
The site is built as a closed and monitored communication platform, featuring a dark homepage with a form for submitting a Signal ID and email address. This design choice indicates an intent to establish a private and ostensibly secure communication channel, operating outside of conventional networks, and requires the preliminary identification of its users.
The inclusion of a validation modal featuring a 64-digit Tracking ID clarifies that this is not an arbitrary platform, such a long and unique identifier enables the precise identification, linking, and monitoring of every single user or “activist” accessing or requesting entry to the site.
Functionally, this setup provides a secure, internal “War Room” infrastructure for cyber groups operating in service of Iranian objectives, complete with a high capacity for internal surveillance and control.
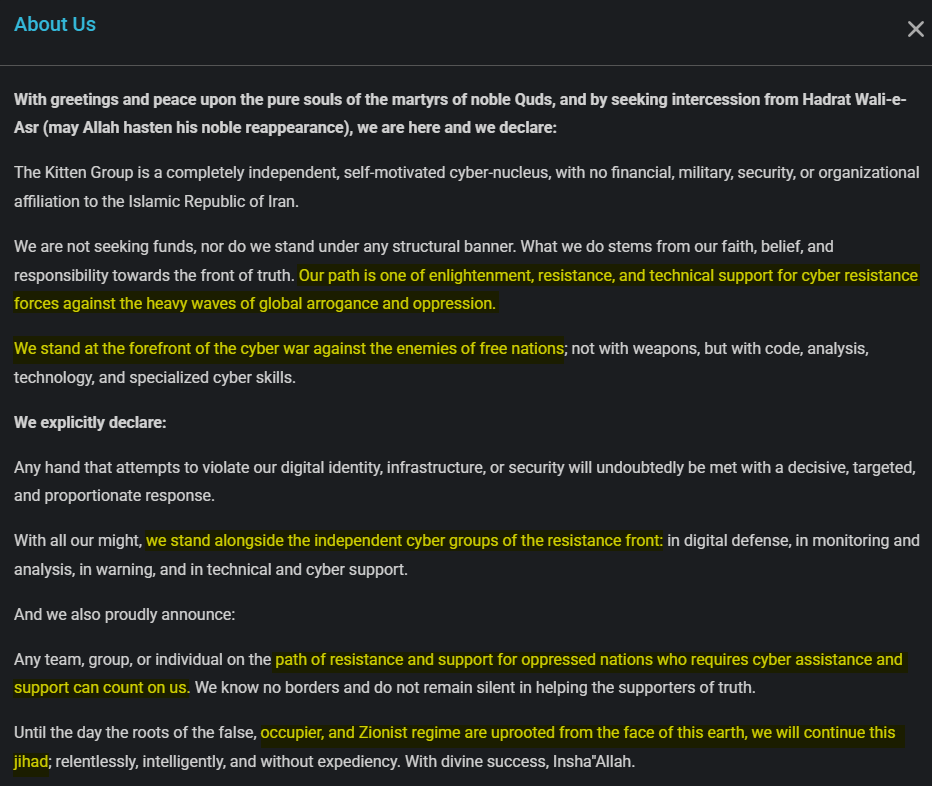
Despite its claims of “independence” within the About Us section, the site’s public declaration is saturated with explicit pro-Iranian ideological markers. The use of terminology such as “The Front”, “The Resistance”, and “Jihad” is fundamental terms within the narrative of the Islamic Revolutionary Guard Corps (IRGC) and the Iranian-led Shiite Axis. Furthermore, the explicit call to action, declaring support for cyber groups operating against the “Zionist regime,” clearly positions the website as an active component of the Iranian non-state actors’ warfare apparatus, even if its institutional affiliation is unofficial or concealed. This makes the platform an ideological front aimed at recruiting and coordinating activists against Israel.
The website directly mentions three known hacking groups that attacked Israel and its allies multiple times, which shows their association with the kitten website.
Clues of Financial Ties With IRGC
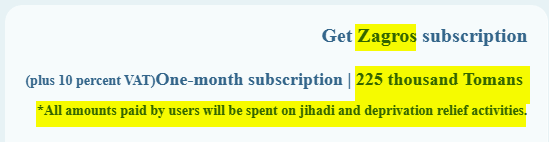
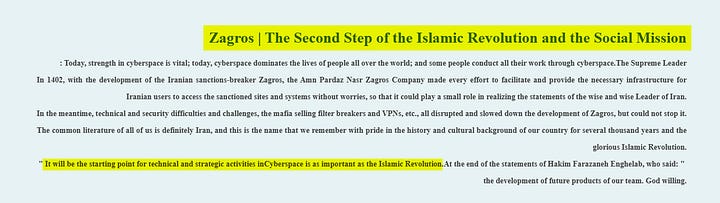
The company frames Zagros as far more than just a technical utility, positioning it as a strategic asset with deep ideological ties to the regime. The developers categorise the service as “The Second Step of the Islamic Revolution and the Social Mission”, with the intent to provide the necessary infrastructure for Iranian users to access sanctioned content so that it can “play a small role in realising the statements of the wise and wise Leader of Iran”. This ideological commitment is also reflected in its financial model, as all funds paid by users for the subscription service are explicitly stated to be spent on “jihad and deprivation relief activities”, linking the service’s commercial revenue directly to the IRGC’s funding and social initiatives.
Hidden Pages, Open Road
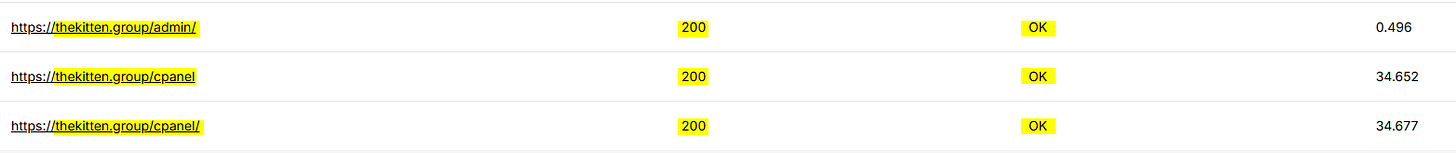
When trying to understand the different pages I can access in this website, I tried URL fuzzing techniques, a thing that revealed two unrestricted, but yet, very sensitive pages with the status code 200 (OK) – admin & cPanel.
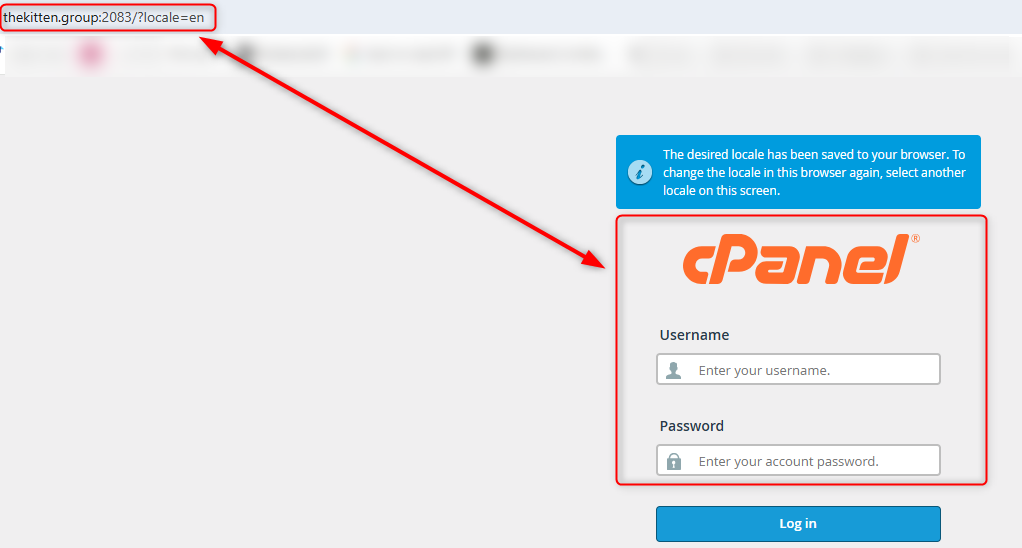
The cPanel (login page for the control panel) runs on port 2083, requires login credentials that I’m not sure if configured with OTP that will alert the suspects, so I chose the second-best option.
Inside The System
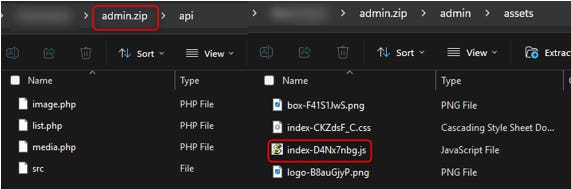
Since the admin page is also accessible, I was able to download the actual admin.zip file and review it for further understanding of the system and architecture of the website.
The availability of this file for download meant that I was able to obtain a complete production build of the administration interface. The bundle exposed all frontend logic, including business flows, routing structure, and the communication patterns used by the client when interacting with the backend. This constitutes an unintended information disclosure that provides detailed insight into the internal structure of the administration system.
The file revealed all API endpoints used by the admin panel, including those responsible for viewing, editing, deleting, uploading, and downloading data, as well as additional administrative operations.
It also exposed the authentication flow, including cookie-based session handling, CSRF mechanisms, and the exact request/response formats the client and server expect.
This information provided me with the understanding of how login is performed, how the authenticated state is maintained, and which backend interactions are critical to the system’s operation.
With these data pieces, if I wanted, I could focus directly on high-value operations such as authorisation checks, potential authentication bypass attempts, IDOR testing, and targeted probing of sensitive actions, including deletions, updates, and file handling.
Technical Analysis of The Code
The code exposes the internal admin API through an Axios client configured with baseURL: “/api/admin/” and withCredentials: true. Directly visible endpoints include, for example, POST /api/admin/view-client for retrieving client data by tracking_id, and GET /api/admin/view-clients for listing all clients.
Additional operations, such as file upload, file deletion, message handling, and project management, are also explicitly mapped (POST /api/admin/upload-files, GET /api/admin/get-projects). The authentication flow is similarly exposed through endpoints such as GET /api/admin/checking, POST /api/admin/login, and POST /api/admin/logout.
Admin interface routes (React Router) are fully visible in the bundle. Examples include /admin/home for the main dashboard, /admin/pro-iran-projects for project management, and /admin/view-request/:tracking_id for viewing a specific request based on a route parameter. These routes reveal the exact internal structure and navigation logic of the admin panel.
Client and request data retrieval are handled directly through service functions defined in the code. For instance, POST /api/admin/view-client is used to load a specific client’s details and GET /api/admin/view-clients returns a list of all clients. The code also exposes how updates are performed, such as POST /api/admin/update-status for modifying a client’s status. These functions demonstrate the precise request formats and expected backend responses.
Online Appearance and Digital Exposure
Once I saw the association and connection between the platforms and understood it is no more than a front for cyber-terror activities, I started to map the footprint of these entities, to check if I could find numbers, emails or even a real person associated with this operation.
Since Zagros platform was the first lead, that was my starting point in this discipline.
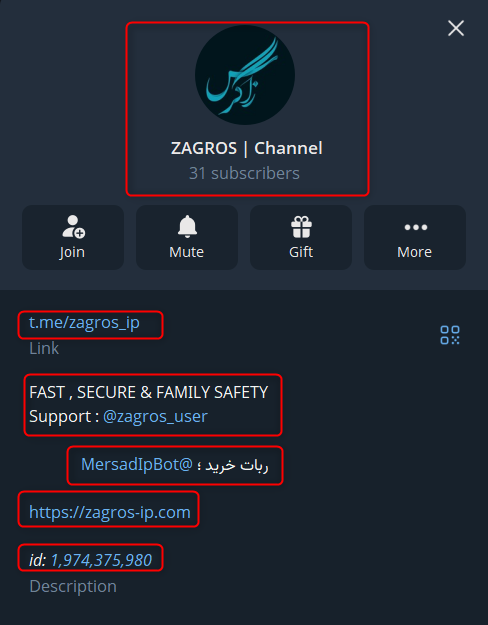
I was managed to find a Telegram channel of Zagros IP, under the name “ZAGROS | Channel”, with their official logo, that counts 31 subscribers. Already claims to be a front shell, with barely any actual activity. The BIO contains direct reference to their website, and two different Telegram bots, one for support and the second for purchasing.
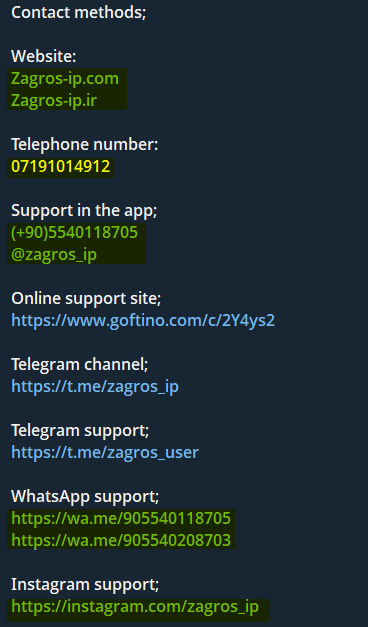
While reviewing old messages in their channel, I found one that particularly stood out, containing two different phone numbers for WhatsApp contact, an Instagram account, and an official phone number.
All numbers are virtual SIM cards, originating from Turkey and registered to WhatsApp only, with no previous activity of any kind, so this lead wasn’t very useful. The users also didn’t provide any relevant information, but then I thought - if Zagros is a front shell for the kitten’s platform, whoever created Zagros is the owner of the operation, or at least, co-owner. So that’s what I did.
Attribution Begins with a Single Domain
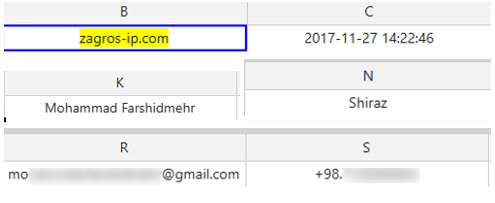
The domain zagros-ip[.]com was part of a data leak from 2018, and revealed a person under the name Mohammad Farshidmehr, an Iranian citizen from Shiraz city.
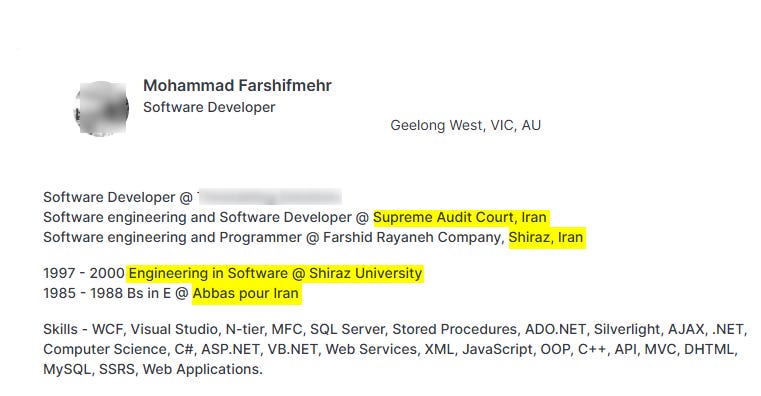
The individual appears to be a web designer and software developer, living in Australia these days, as appeared on his resume.
With a deeper search, I was managed to find a website he created himself, as part of self marketing act. The website contained a symbol (logo) created by himself, possibly a kind of hallmark.
The first symbol, taken from Mohammad’s website, uses modern Iranian calligraphy identical to the style found in the official emblem of ZAGROS, the Iranian cyber entity operating as a cover for offensive activity and for supporting anti-Israeli proxy groups.

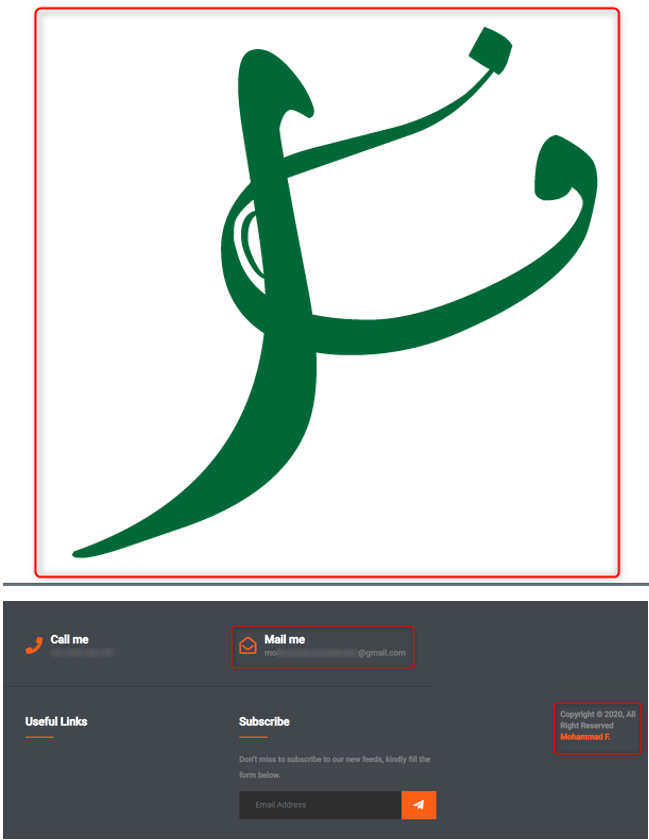
Both symbols rely on the same graphic pattern: Persian line flow, three-dimensional volume construction, curved letterforms resembling the “ʿayn / z” shapes characteristic of Iranian calligraphic design, and colour usage consistent with the same visual school.
This graphic overlap is not coincidental, but a reflection of design style commonly associated with Iranian studios working for government-affiliated bodies and pro-Iranian cyber organisations.
The Facade That Tells the Truth
In practice, the zagrosguard[.]ir domain presents as a relatively simple landing page, with a significant lack of robust and independently verifiable commercial identity. Its stated operational complexity and ideological mission appear to heavily outweigh its minimal public-facing corporate infrastructure.
Based on this observation, it is highly probable that the public-facing Zagros site primarily functions as a technological front or a marketing vehicle for an entirely different, perhaps deeper, network or underlying service.
This approach allows the operating entity, the Amn Pardaz Nasr Zagros Company, to maintain a strategic distance from its core network infrastructure while simultaneously presenting a sanctioned, ideological, and consumer-friendly interface to domestic users.